Merkle tree is a binary, hash tree–like data structure. In a binary tree, a node can have a maximum of two child nodes — a left node and a right node. Each leaf node of the Merkle tree stores the hash value of a data element. When we know the data of the left node and the right node, we can calculate the complete information of the parent node. This comprehensive information consists of two sections: Balance data of the wallet address, and hash data.
-
Balance data: Based on the data structure of the binary tree, the balance data of the parent node can only be composed of the balance data of both the left and right nodes under it.
-
Hash data: Each node includes balance data, hierarchical data of the binary tree (dotted line in the figure) and hash data of child nodes (data of left node and right node are stored under each node).
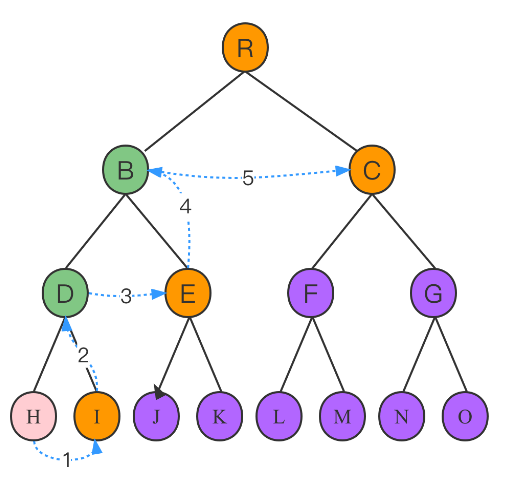
The Merkle tree is verified by calculation, such as the green parts (B and D) calculated in the picture above, and by the following two criteria:
1. Verify whether the balance meets the splitting principle.
2. Verify whether the hash is legal.
The Merkle tree uses a hash function, which allows users to verify whether they’re part of the complete tree without knowing the information in the purple nodes. Merkel proofs are unique to individual users. In the case of a Merkle tree with 24 levels, the users need a balance array with a length of 24 elements to verify their balance information, and this array is only used to verify the user's balance.
As long as the data obtained by users doesn’t exceed 50% of the total user data in the Merkle tree, users cannot reconstruct the entire data structure based on their own fragmented information. Therefore, for the company, the Merkle tree ensures that the company's overall asset information won’t be leaked, and that users’ account privacy is protected.
Bybit provides two verification methods as follows:
Verification via the Bybit Platform
You can visit this page to enter the Verify My Account page and view your Merkle path. We graphically display the node derivation process of Merkle tree verification to make it easier for you to view your assets balances.
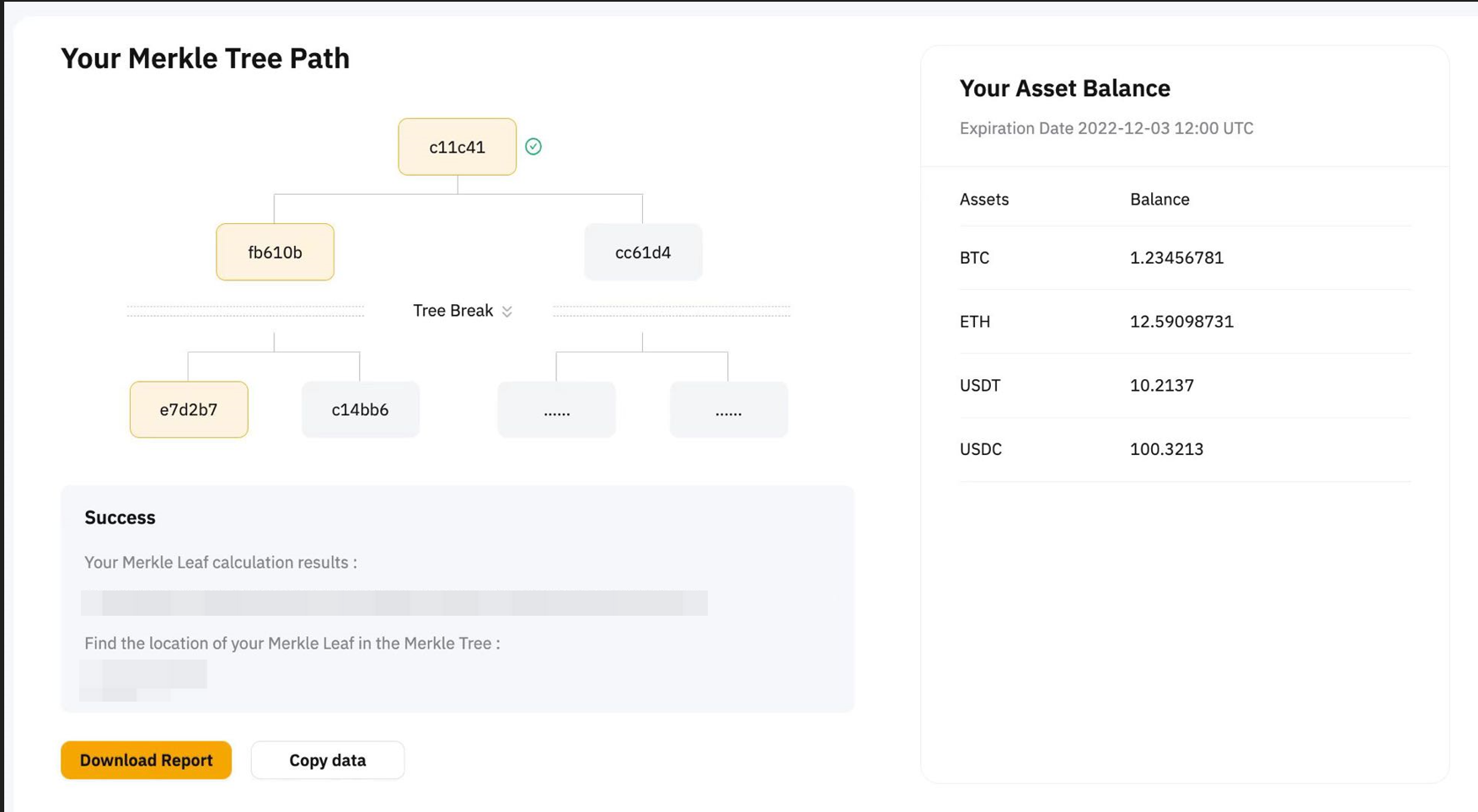
Note: We conduct regular Proof of Reserves audits to demonstrate that Bybit holds adequate reserves. If you created your account after an audit was conducted or you do not hold audited tokens, there will not be any corresponding audit records for your account.
Via Self Validation Tool — Open Source Code
Bybit has released its Merkle tree generation source code and verification code on GitHub to assist users in their own balance verification process. The calculation process of the Merkle tree involves the calculation of massive user data, which is usually implemented by big data and Java. The Java coding is completely open for users to inspect.
Background
Bybit has open-sourced the following codes for professional users to self-verify. Users can click on Copy Data from their Proof of Reserve page to copy the data to the Merkle tree proof file on their own programming system clipboard, and store it as a file named myProof.json on their local drive.
How to Proceed
1. Build Your Executable File
Please download the latest source code files, and ensure that JDK (version 1.8 and above) and Maven have been installed in your workstation or laptop.
-
Resolve dependencies, compile and package.

-
Check the compiled jar package, as follows, in the project current folder.
2. Perform Your Verification
-
You can paste the proof file copied from the Bybit website into a new file in the current folder, and name the file as myProof.json. Then, execute the following command:
-
Next, you can run the verified program and observe its output data.